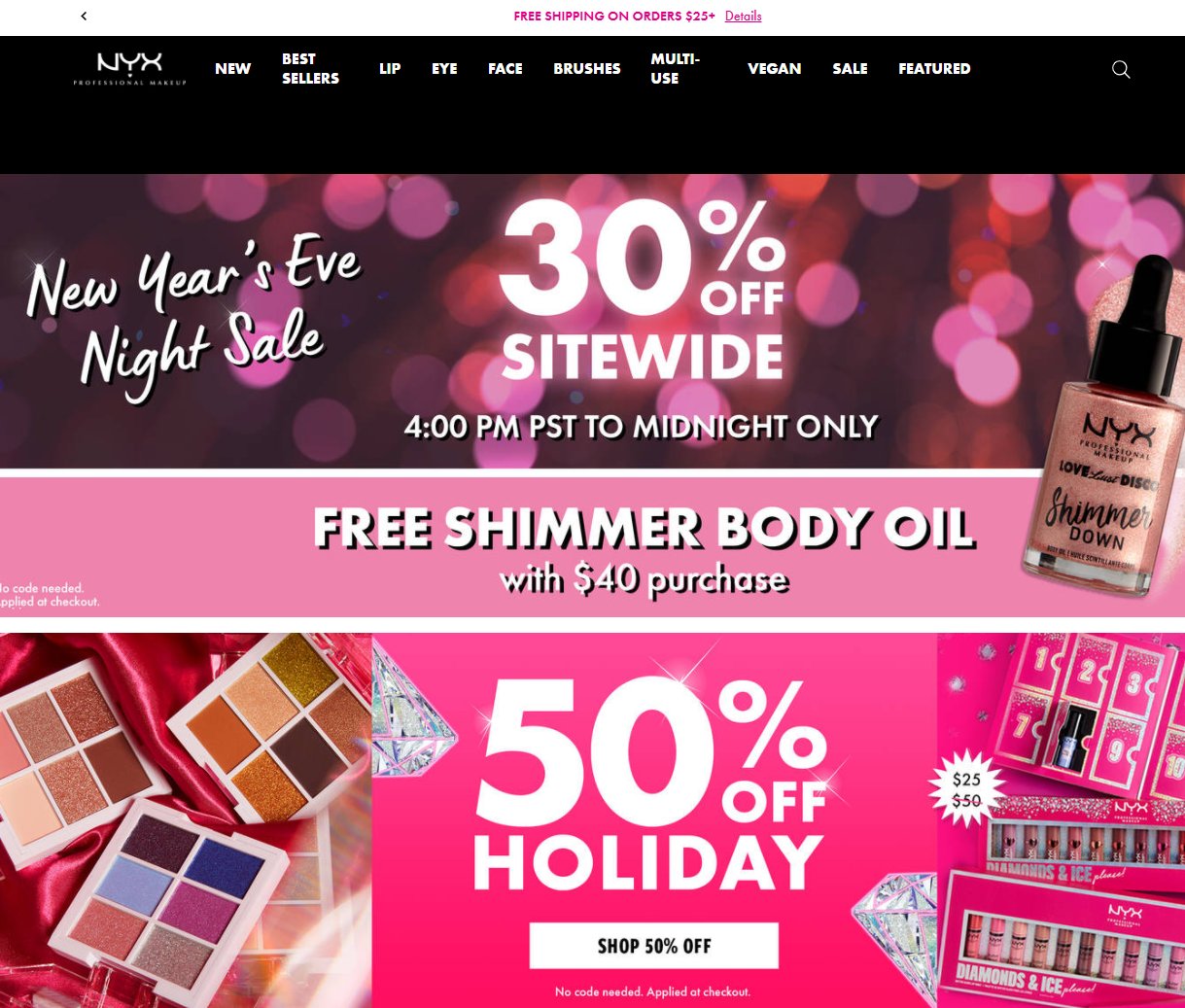
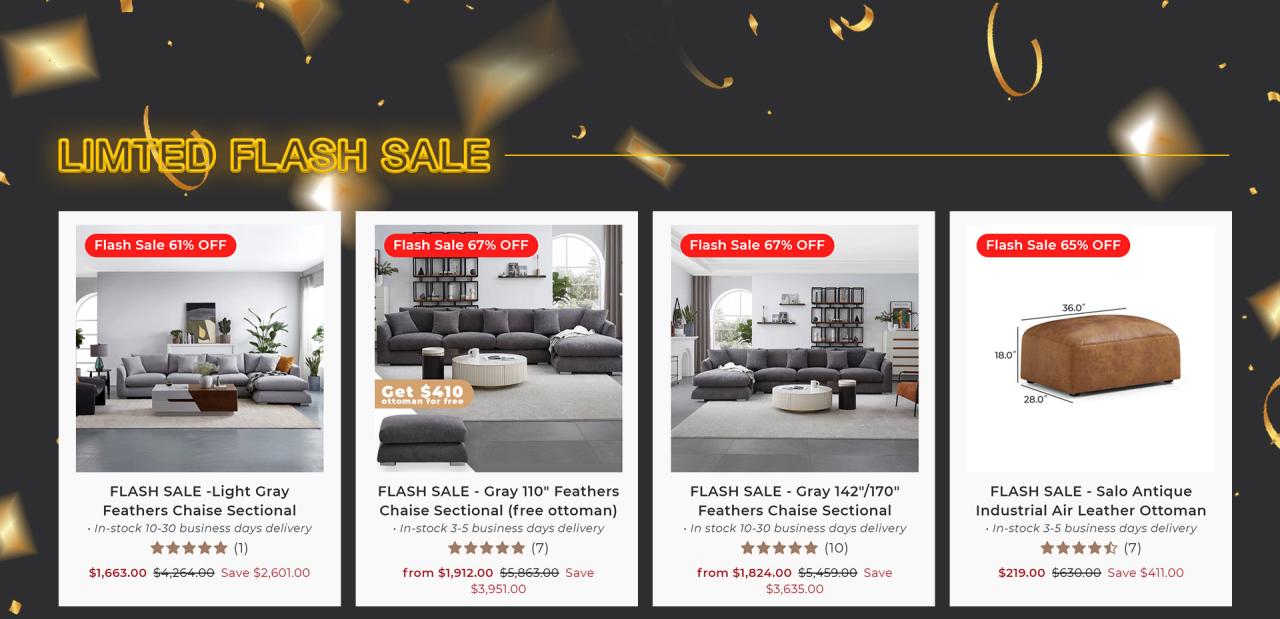
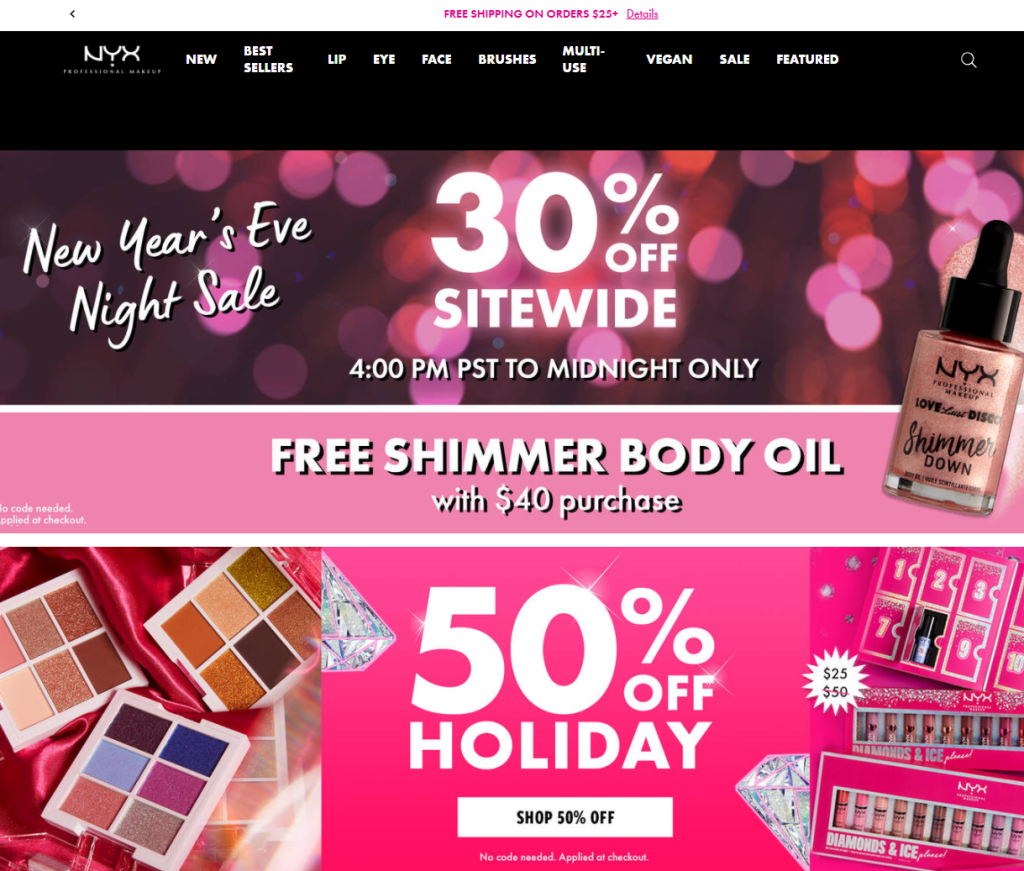
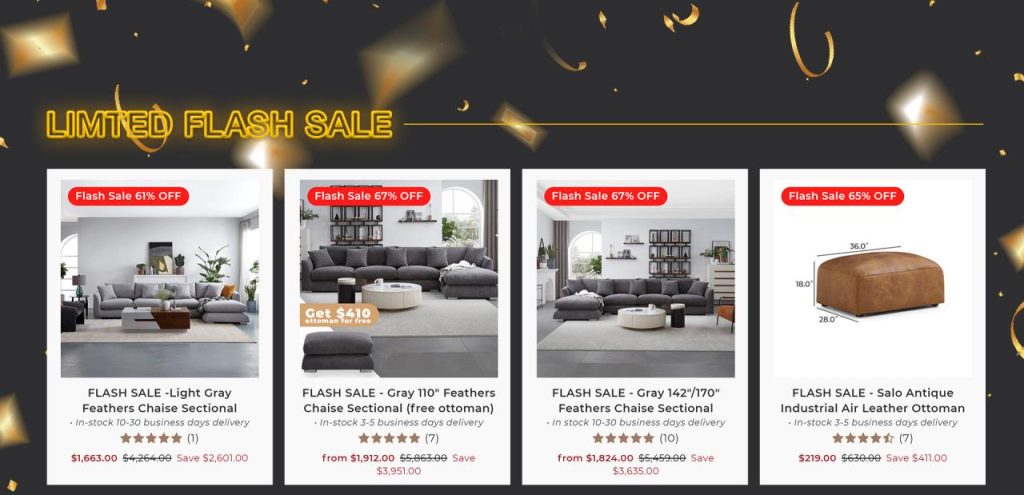
Is flash sale 12 legit is a question that resonates with many consumers eager to find great deals while navigating the complexities of online shopping. In an age where discounts can be enticing yet elusive, understanding the legitimacy of flash sales becomes crucial. This inquiry leads us into the intriguing world of flash sales, uncovering the dynamics that define them and the factors consumers should consider before making a purchase.
The significance of evaluating the legitimacy of sales events like flash sale 12 cannot be overstated. With the rise of e-commerce, discerning which offers are genuine has become essential for shoppers aiming to secure the best prices without compromising their security or satisfaction. This exploration will delve into various aspects of flash sales, including their operational mechanics, common concerns, and how to identify trustworthy deals.
In the ever-evolving landscape of technology, the importance of cybersecurity continues to rise. With an increasing number of devices connected to the internet and the rapid advancement of technology, organizations and individuals alike must prioritize protecting their data and digital assets. This article aims to explore the various aspects of cybersecurity, its significance, the common threats faced, and strategies to bolster security measures.To begin with, it is essential to define what cybersecurity entails.
Cybersecurity refers to the practice of protecting systems, networks, and programs from digital attacks. These cyberattacks typically aim to access, change, or destroy sensitive information; extort money from users; or disrupt normal business operations. As technology progresses, the methods employed by cybercriminals also become more sophisticated, making it imperative for everyone to understand and implement effective cybersecurity measures.One of the main reasons cybersecurity is crucial is the rising prevalence of data breaches.

A data breach occurs when unauthorized individuals gain access to confidential data, typically involving personal identification information (PII), financial records, or intellectual property. According to various reports, millions of records are compromised each year, leading to significant financial losses and a loss of trust for affected organizations. The repercussions of a data breach can be devastating, not only for companies but also for individuals whose information is compromised.Moreover, the financial implications of cybercrime are staggering.
The cost of cybersecurity breaches has been reported to run into trillions of dollars globally, encompassing not only direct financial losses but also legal fees, regulatory fines, and reputational damage. Organizations may face lawsuits from affected parties, and customers may choose to take their business elsewhere following a breach. To mitigate these risks, it is essential for companies to invest in robust cybersecurity measures.In addition to data breaches, various other cyber threats exist that can compromise the integrity of information systems.
Malware, which includes viruses, worms, and ransomware, is one of the most common forms of cyber threats. Malware is designed to infiltrate and damage computers without the owner’s consent, resulting in data loss or unauthorized access to sensitive information. Ransomware, a specific type of malware, encrypts files on the infected system and demands a ransom payment for decryption. This type of attack has become increasingly prevalent, with organizations across various sectors falling victim to ransomware attacks.Phishing is another significant threat in the realm of cybersecurity.
Cybercriminals use deceptive emails, messages, or websites to trick individuals into revealing personal information, such as passwords or credit card numbers. Phishing attacks can be highly sophisticated, often appearing to come from trusted sources. Consequently, it is crucial for individuals to remain vigilant and skeptical of any unsolicited communications requesting sensitive information.To combat these threats, organizations must adopt a comprehensive cybersecurity strategy.
This strategy should encompass a multi-layered approach that includes prevention, detection, and response measures. The first line of defense involves implementing firewalls and antivirus software to prevent unauthorized access to systems. Regular updates and patches should also be applied to software and operating systems to ensure vulnerabilities are addressed promptly.Employee training is another critical component of an effective cybersecurity strategy.
Human error remains one of the leading causes of data breaches; therefore, educating employees on best practices for cybersecurity is vital. Organizations should conduct regular training sessions to raise awareness about common threats, including phishing and social engineering attacks. By fostering a culture of cybersecurity awareness among employees, organizations can significantly reduce the likelihood of successful attacks.In addition to preventive measures, organizations must also invest in detection tools to identify and respond to security incidents swiftly.
Intrusion detection systems (IDS) can monitor network traffic for suspicious activity and alert administrators to potential threats. Furthermore, businesses should develop an incident response plan outlining specific steps to take in the event of a cyber incident. This plan should include communication protocols, damage assessment procedures, and recovery strategies.Another important aspect of cybersecurity is data encryption. Encrypting sensitive data ensures that even if cybercriminals gain access to it, they cannot read or use the information without the decryption key.
Organizations should prioritize encrypting data both at rest and in transit to safeguard against unauthorized access.Regular security assessments and audits are also essential to ensuring the effectiveness of cybersecurity measures. Organizations should perform vulnerability assessments to identify potential weaknesses in their systems and take corrective actions accordingly. Additionally, penetration testing can simulate cyberattacks to evaluate the resilience of security measures and provide valuable insights for improvement.In conclusion, the importance of cybersecurity cannot be overstated in today’s digital age.
With the increasing frequency and sophistication of cyberattacks, individuals and organizations must take proactive measures to safeguard their data and digital assets. By understanding the common threats, investing in preventive measures, fostering a culture of awareness, and implementing a comprehensive cybersecurity strategy, it is possible to mitigate risks and protect against the devastating consequences of cybercrime. As we move forward in this digital era, prioritizing cybersecurity will be crucial for ensuring the safety and integrity of our information systems.
Query Resolution
What are flash sales?
Flash sales are limited-time promotions where products are offered at significantly reduced prices, designed to encourage quick purchases.

How can I verify if a flash sale is legitimate?
To verify a flash sale’s legitimacy, check the seller’s reputation, read customer reviews, and review the terms and conditions of the sale.
Are there risks associated with flash sales?
Yes, risks include potential scams, receiving counterfeit products, and the possibility of misleading marketing practices.
Do flash sales always offer the best prices?
Not necessarily; while they can offer significant discounts, it’s important to compare prices and ensure that the deal is truly beneficial.
How can I protect myself while shopping during flash sales?
To protect yourself, shop only from reputable websites, use secure payment methods, and be cautious about sharing personal information.